Security researchers have identified a new phishing platform, Quantum Route Redirect (QRR), targeting Microsoft 365 users across nearly 1,000 domains in 90 countries, raising concerns about account security.
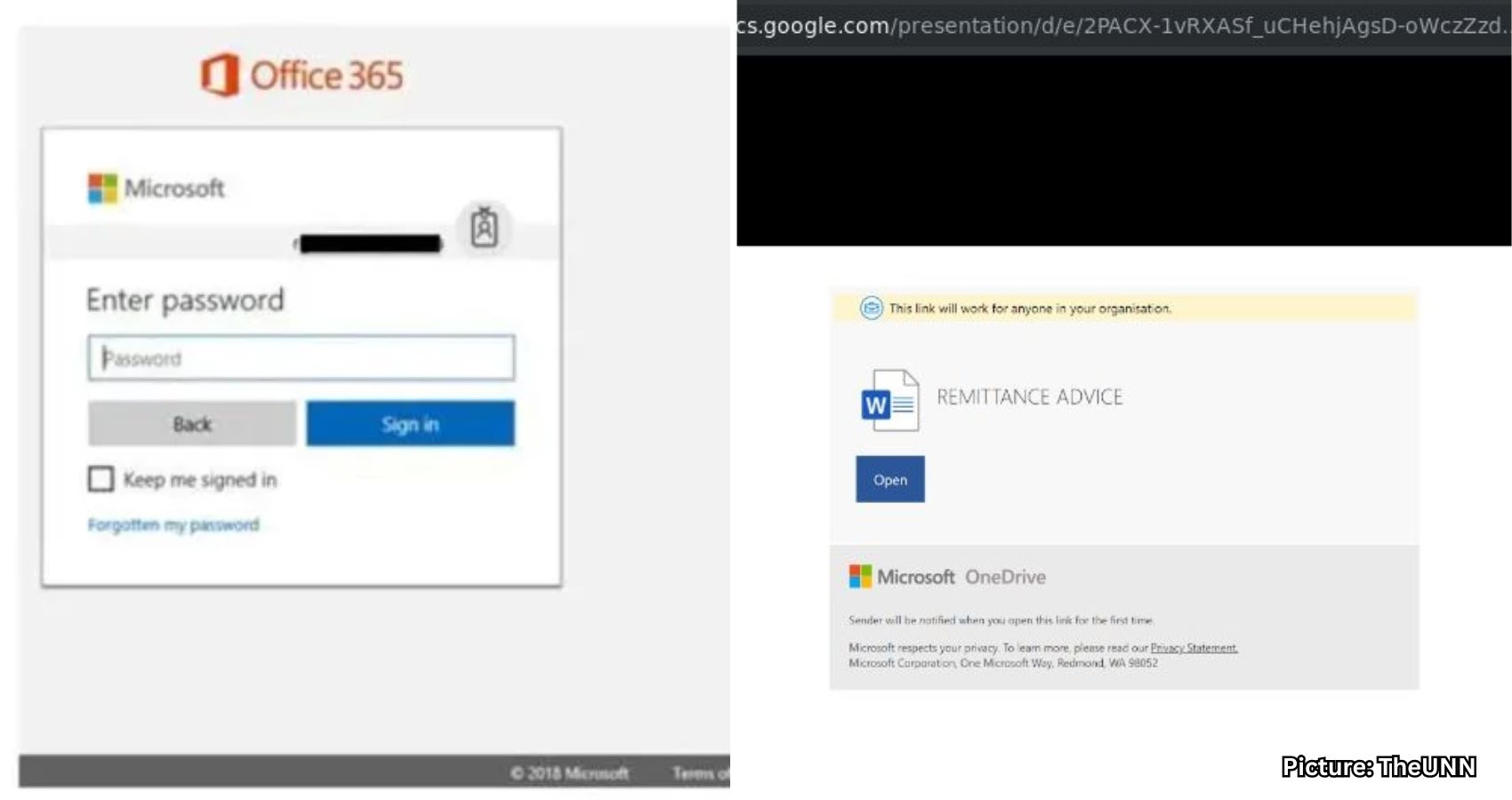
Cybersecurity experts have uncovered a significant phishing operation that specifically targets Microsoft 365 users. This new platform, known as Quantum Route Redirect (QRR), is responsible for a surge in fake login pages that are hosted on approximately 1,000 different domains. These pages are designed to deceive users and evade detection by automated security scanners.
The QRR phishing scheme employs realistic email lures that mimic legitimate communications, such as DocuSign requests, payment notifications, voicemail alerts, and QR-code prompts. Victims who engage with these messages are redirected to counterfeit Microsoft 365 login pages, where their usernames and passwords are harvested by the attackers. Many of these fraudulent pages are hosted on parked or compromised legitimate domains, which can create a false sense of security for unsuspecting users.
Researchers have tracked QRR’s activities across 90 countries, with approximately 76% of the attacks targeting users in the United States. This extensive reach positions QRR as one of the largest phishing operations currently in existence.
The emergence of QRR follows Microsoft’s successful disruption of a major phishing network known as RaccoonO365. This previous operation was notorious for selling ready-made Microsoft login copies that were used to steal over 5,000 sets of credentials, including accounts associated with more than 20 U.S. healthcare organizations. Subscribers to RaccoonO365 could pay as little as $12 a day to send thousands of phishing emails.
In response to the RaccoonO365 operation, Microsoft’s Digital Crimes Unit managed to shut down 338 related websites and identified Joshua Ogundipe from Nigeria as the operator. Investigators linked him to the phishing code and a cryptocurrency wallet that had amassed over $100,000. Subsequently, Microsoft and Health-ISAC filed a lawsuit in New York, accusing Ogundipe of multiple cybercrime violations.
QRR builds on the tactics of other phishing kits, including VoidProxy, Darcula, Morphing Meerkat, and Tycoon2FA, by incorporating advanced automation, bot filtering, and a user-friendly dashboard that enables attackers to execute large-scale campaigns quickly and efficiently.
The QRR platform utilizes around 1,000 domains, many of which are real sites that have either been parked or compromised. This strategy helps the phishing pages appear legitimate at first glance. The URLs used in these scams often follow predictable patterns that can mislead users into believing they are accessing a safe site.
One of the key features of QRR is its automated filtering system, which detects bot traffic. This system directs automated scanners to harmless pages while routing real users to the credential-harvesting sites. Attackers can manage their campaigns through a control panel that logs traffic and activity, allowing them to scale their operations rapidly without requiring extensive technical skills.
Security analysts emphasize that organizations can no longer rely solely on URL scanning to protect against phishing threats. Instead, they advocate for layered defenses and behavioral analysis to identify threats that employ domain rotation and automated evasion tactics.
When attackers gain access to a Microsoft 365 login, they can view emails, access files, and even send new phishing messages that appear to originate from the victim’s account. This can initiate a chain reaction, spreading the threat further. To mitigate risks from fake Microsoft 365 pages and look-alike emails, users are encouraged to adopt several protective measures.
First, it is crucial to verify the sender’s email address. Look for slight misspellings, unexpected attachments, or unusual wording, as these can be indicators of a phishing attempt. Before clicking on any links, hover over them to preview the URL. If it does not lead to the official Microsoft login page or appears suspicious, it is best to avoid it.
Implementing multi-factor authentication (MFA) adds an additional layer of security, making it significantly more challenging for attackers to gain access, even if they have the user’s password. Options such as app-based codes or hardware keys can provide robust protection against phishing kits.
Attackers often gather personal information from data broker sites to create convincing phishing emails. Utilizing a trusted data removal service can help scrub personal information from these sites, reducing the likelihood of targeted scams and making it more difficult for criminals to craft realistic phishing alerts.
While no service can guarantee complete removal of personal data from the internet, employing a data removal service is a prudent choice. These services actively monitor and systematically erase personal information from numerous websites, providing peace of mind and enhancing privacy.
Keeping all devices updated is essential, as updates often patch security vulnerabilities that attackers exploit in phishing kits like QRR. When accessing sensitive sites, it is advisable to type the address directly into the browser rather than clicking on links. Strong antivirus software can also provide alerts about fake websites and block scripts used by phishing kits to steal login credentials.
Most email providers offer enhanced filtering settings that can block risky messages before they reach the inbox. Users should enable the highest level of filtering available to reduce the number of fake Microsoft alerts that may slip through.
Additionally, turning on sign-in notifications for Microsoft accounts can alert users to any unauthorized access attempts. This feature can be activated by signing into the Microsoft account online, navigating to Security, selecting Advanced security options, and enabling sign-in alerts for suspicious activity.
The QRR phishing operation serves as a stark reminder of how quickly scammers can adapt their tactics. Tools like this facilitate the rapid deployment of large volumes of convincing fake Microsoft emails. However, by adopting smarter security habits, enabling stronger sign-in protections, and staying informed about the latest phishing strategies, users can significantly reduce their risk of falling victim to these schemes.
Do you believe that most people can distinguish between a genuine Microsoft login page and a counterfeit one, or have phishing kits become too sophisticated? Share your thoughts with us at Cyberguy.com.
Source: Original article